Palo Alto Networks and IBM to Jointly Provide AI-powered Security Offerings
IBM to Deliver Security Consulting Services Across Palo Alto Networks Security Platforms News Summary: IBM to platformize internal security solutions with Palo Alto Networks; Palo Alto Networks will be its preferred cybersecurity partner across network, cloud and SOC Palo Alto Networks will incorporate watsonx large language models (LLMs) in Cortex XSIAM to deliver additional Precision…

Important Leadership Announcement from Vicarius
On May 23rd, 2016, I registered Vicarius LTD as an Israeli entity. As engineers, we immediately started to build something out. The product was quite different from what it is today. The idea was to build a complex permission manager for low-level operating system APIs to block malware families categorically. Customers didn’t understand what the…

AI Squared Acquires Multiwoven to Accelerate Delivery of Data & AI Insights into Business Applications
AI Squared , a leading technology provider for integrating information into web-based business applications, announces its acquisition of the world’s number one open-source Reverse ETL (rETL) company, Multiwoven. With this acquisition, AI Squared furthers its commitment to helping organizations simplify the movement of data and AI insights into business applications. The acquisition of Multiwoven comes…

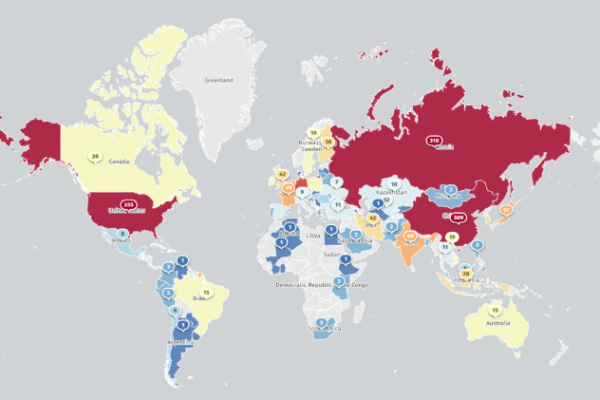
Global Cybersecurity Ranking 2024: Which Countries Are Most at Risk?
A new study found the countries with the highest and lowest risk for cyber threats worldwide in 2024. Cybersecurity experts at mixmode.ai found that Finland ranked first among the lowest-risk countries for Cyber Threats Worldwide, with a Cyber Safety Score of 92.81. In overall cyber safety, Finland has outperformed several major countries, such as the USA, UK,…
CybeReady, Announced an Impactful new feature to its SaaS-based Cybersecurity Learning Platform: a cutting-edge Poster Studio designed to support CISOs in educating employees about a vast array of security threats. The innovative tool enables the creation of customizable educational posters to address critical issues such as phishing, smishing, quishing, ransomware, and a wide range of other potential threats that put organizations at risk. The innovative and easy-to-use poster design feature is a creative and effective method of quickly creating and designing both digital and printed posters. The resulting posters can be leveraged in various ways, for use as desktop wallpapers, announcement screen displays around the office or printed and hung in common areas, providing a constant reminder of cybersecurity best practices. “Our new Poster Studio feature extends the core principles of our Awareness Bites into visually engaging posters that are tailored to be concise and impactful. They are designed not only to educate but to blend seamlessly into various work environments,” said Mike Polatsek, CEO of CybeReady. “Whether it’s on a factory floor or a corporate office, these posters serve as an essential component of a holistic cybersecurity training program.” Key Features of the Poster Studio Tool: – Multichannel Approach: Posters serve as an additional reinforcement channel, supporting diverse learning preferences and enhancing organizational cybersecurity culture. – Positive Learning Experience: The posters are designed to be user-friendly and require only seconds to read, making cybersecurity education straightforward and effective. – Extended Reach: Especially beneficial for non-office staff, the posters can be placed in high-traffic ake cafeterias and washrooms, ensuring that cybersecurity training reaches every corner of the organization. – Customization and Localization: Available in 28 languages, these posters can be customized with an organization’s logo, colors, and specific messaging, making them a perfect fit for any corporate identity. As cyber threats evolve, the necessity for adaptable and comprehensive educational tools becomes increasingly crucial. CybeReady’s commitment to developing innovative solutions, like the poster creation feature, is ideally suited to support the mission of transforming all employees into cyber-aware, vigilant defenders of their organizations’ reas lidigital assets.
CybeReady, a global leader in autonomous cybersecurity learning, today announced an impactful new feature to its SaaS-based Cybersecurity Learning Platform: a cutting-edge Poster Studio designed to support CISOs in educating employees about a vast array of security threats. The innovative tool enables the creation of customizable educational posters to address critical issues such as phishing,…

SentinelOne Redefines Cloud Security; Launches Revolutionary CNAPP with unique Offensive Security Engine
Attackers are targeting the scope and scale of the cloud to run rapid and coordinated threat campaigns. A new approach is needed to defend against them, SentinelOne (NYSE: S), a global leader in AI-powered security, is delivering it, with the launch of Singularity Cloud Native Security. A revolutionary solution built on SentinelOne’s acquisition of PingSafe…

El Salvador Suffered a Massive leak of Biometric Data.
Virtually the entire population of a country has been affected by a compromise of biometric data. A threat actor leaked the personally identifiable information (PII) of over five million citizens from El Salvador on the Dark Web, impacting more than 80% of the country’s population. The threat actor, going by the alias ‘CiberinteligenciaSV,’ posted the 144 GB data dump…

Dinesh Kamble joins as CISO & Head Infosec at RBL Bank
In order to strengthen the organization’s defenses and promote a resilient culture, Dinesh Kamble has joined RBL Bank as the CISO and Head Infosec. Having worked in a variety of industries for more than 20 years, Kamble brings a plethora of knowledge to his current position and is well-positioned to guide RBL Bank through the…

UK & Allies Sanction Prolific Cyber Hacker; Leader of LockBit
The UK, US and Australia have sanctioned the Russian leader of cyber-crime gang LockBit. UK, US and Australia sanction Russian leader of cyber-crime gang LockBit LockBit were one of the most prolific ransomware groups in recent years, responsible for attacks on over 200 UK businesses and major public service providers UK and Allies crack down…

GMMCO Appointed Ganesan Sivaramakrishnan, as Head IT & SAP operations
In a move signaling a focus on IT and digital transformation, GMMCO has appointed a seasoned IT leader, Ganesan Sivaramakrishnan, to head its IT and SAP operations. Ganesan Sivaramakrishnan brings over 25 years of experience to GMMCO, having previously served as Head of IT, SAP and Digital Initiatives at BGR Group. During his tenure at…