The sixth edition of the annual Sophos State of Ransomware report which reveals the reality of ransomware in 2025.This year’s report details how organizations’ experiences of ransomware— both cause and consequences — have evolved over the last 12
months.
It also shines light into previously unexplored areas, including the operational factors that left organizations exposed to attack and the human impact of incidents on the IT/cybersecurity team.
The report is based on the findings from an independent, vendor-agnostic survey into organizational experiences of ransomware that was commissioned by Sophos and conducted by a third-party specialist between January and March 2025. All respondents work in organizations with between 100 and 5,000 employees and were asked to answer based on their experiences in the previous 12 months.
Participants came from 17 countries and a wide range of industries, ensuring that the survey results reflect diverse experiences across the public and private sectors.
Key findings
Why organizations fall victim to ransomware?
For the third year running, victims identified exploited vulnerabilities as the most
common technical root cause of attack, used in 32% of incidents.
Multiple operational factors contribute to organizations falling victim to ransomware, with the most common being a lack of expertise, named by 40.2% of victims.
It is followed in very close succession by having security gaps that the organization was not aware of, which was a contributing factor in 40.1% of attacks.
In third place was lack of people/capacity, which contributed to 39.4% of attacks.
What happens to the data
Data encryption is at the lowest level in six years, with 50% of attacks now resulting in data encryption, down from 70% in 2024.
28% of organizations that had data encrypted also experienced data exfiltration.
97% that had data encrypted were able to recover it.
The use of backups to restore encrypted data is at the lowest rate in six years, used just in 54% of incidents.
49% of victims paid the ransom to get their data back. While this represents a slight drop
from last year’s 56%, it is the second highest ransom payment rate in six years.
Ransoms: Demands and payments
The average (median) ransom demand has dropped by one third (34%) over the
last year, coming in at $1,324,439 in 2025 compared to $2 million in 2024.
The average (median) ransom payment has fallen by 50% in the last year, down from $2M in 2024 to $1M in 2025. The primary factor behind this drop is a reduction in the percentage of ransom payments of $5M or more, down from 31% of payments in 2024 to 20% in 2025.
When comparing demands vs. payments, only 29% said their payment matched
the initial demand. 53% paid less than the initial ask while 18% paid more.
Business impact of ransomware
Excluding any ransom paid, the average cost to recover from a ransomware attack dropped by 44% over the last year, coming in at $1.53 million, down from $2.73 million in 2024.
Looking at speed of recovery, organizations are getting faster, with 53% fully recovered after a week, up from 35% in 2024.
Human impact of ransomware
Every organization that had data encrypted reported that there were direct repercussions for the IT/cybersecurity team:
41% of IT/cybersecurity teams say they have increased anxiety or stress about future attacks.
One third (34%) said the team experienced feelings of guilt that the attack was not stopped in time.
40% report increased pressure from senior leaders but 31% report increased recognition.
31% of teams have experienced staff absence due to stress/mental health issues related to the attack.
In one quarter of cases, the team’s leadership was replaced as a consequence of the attack
Why organizations fall victim to ransomware
Technical root cause of attacks
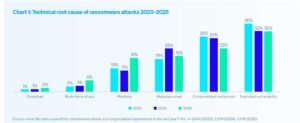
For the third year running, victims identified exploited vulnerabilities as the most common root cause of ransomware incidents, used to penetrate organizations in 32% of attacks overall.
Compromised credentials remains the second most common perceived attack vector, although the percentage of attacks that used this approach dropped from 29% in 2024 to 23% in 2025.
Email remains a major vector of attack with 19% of victims reporting malicious email as the root cause and a further 18% citing phishing — a notable jump from last year’s 11%.
The research reveals differences in attack vectors based on organization size:
Compromised credentials were the most common root cause in the 100–250 employee segment, used in 30% of attacks.
40% of attacks in the 501–1,000 employee segment started with an exploited vulnerability.
Approaching one quarter (23%) of attacks on organizations with 1,001–3,000 employees began with a phishing email.
Operational root cause of incidents
This year’s report explores for the first time the organizational factors that left companies exposed to attacks.
The findings reveal that victims are typically facing multiple operational challenges with respondents citing 2.7 factors, on average, that contributed to them falling victim to the ransomware attack.
Overall, there is no single stand-out source, with the organizational root causes very
evenly split across protection issues, resourcing issues, and security gaps.