The Trellix Advanced Research Center has uncovered a sophisticated APT malware campaign that we’ve dubbed OneClik. It specifically targets the energy, oil, and gas sector through phishing attacks and the exploitation of Microsoft ClickOnce. The campaign exhibits characteristics aligned with Chinese-affiliated threat actors, though attribution remains cautious. Its methods reflect a broader shift toward “living off the land” tactics, blending malicious operations within cloud and enterprise tooling to evade traditional detection mechanisms.
This stealthy operation unfolds across three distinct variants (v1a,BPI-MDM, andv1d), each using a .NET-based loader (“OneClikNet“) to deploy a sophisticated Golanguage backdoor (“RunnerBeacon“) that communicates with threat actor infrastructure hidden behind legitimate AWS cloud services [3] (CloudFront, API Gateway, Lambda). This makes network-based detection nearly impossible without decryption or deep behavioral analysis.
Our analysis reveals how this campaign has progressively evolved with advanced evasion tactics and C2 obfuscation across each variant. Key findings include abuse of ClickOnce [1] to proxy execution, early injection via .NET AppDomainManager hijacking [2], and anti-analysis measures (anti-debugging loops and sandbox detection).
ClickOnce abuse background
ClickOnce is a Microsoft .NET deployment technology that allows self-updating applications to install and run from remote sources. Although intended for ease of deployment, adversaries can abuse ClickOnce for stealthy code execution [1].
ClickOnce apps launch under the Deployment Service (dfsvc.exe), enabling attackers to proxy execution of malicious payloads through this trusted host. Because ClickOnce applications run with user-level privileges (no user account control required), they offer an appealing delivery mechanism for threat actors aiming to avoid privilege escalation.
In OneClik, attackers sent emails with links to a fake “hardware analysis” site. Visiting the site led to a ClickOnce manifest (an .application file)—cloaked as a legitimate tool—silently downloading and executing. Once launched, the ClickOnce loader injects malicious code via .NET configuration tampering.
Specifically, the loader uses AppDomainManager hijacking (T1574.014) by crafting the .exe.config settings to load a remote malicious DLL at CLR startup [2]. This technique (“AppDomainManager injection”) causes the legitimate .NET executable (e.g.ZSATray.exe, umt.exe or ied.exe) to load an attacker-controlled assembly instead of its normal dependencies. With the loader in place, payload execution proceeds under dfsvc.exe, blending with benign ClickOnce activities.
Infection chain and technical analysis
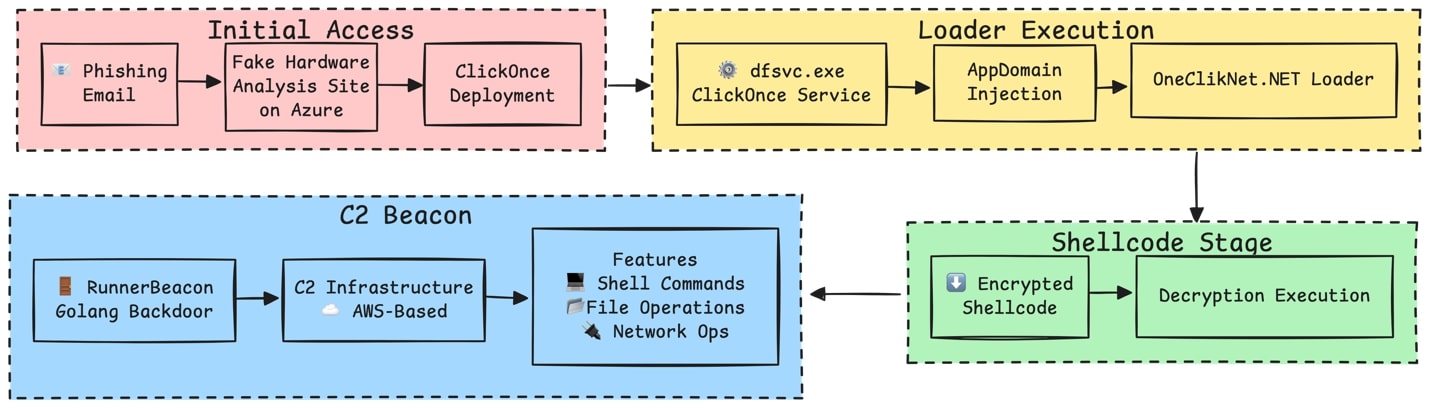 Figure 1: Campaign infection chain
Figure 1: Campaign infection chain
The OneClik campaign’s infection chain unfolds in stages (Figure 1). In the v1a variant, the victim visited a phishing link from an email (e.g. analysis.html on an Azure Blob Storage) fetched [victim]_Hardware_Analysis_Tool.application. This launched [victim]_Hardware_Analysis_Tool.exe under dfsvc.exe, which in turn loaded a sidecar binary via compiled ClickOnce manifest (cdf-ms) hijack.
That legitimate binary (ZSATray.exe) was then run with a tempered .config. This secondary stage downloaded a .NET DLL and an encrypted shellcode (download temp.dat and fav.ico base64 blob respectively) into memory, eventually injecting a Golang based backdoor (the RunnerBeacon).
In addition to remote malicious DLL side load in v1a and v1d, the loader employs AppDomainManager hijacking by embedding <appDomainManagerAssembly> and <appDomainManagerType> entries in its .config (Code 2), pointing to a local malicious DLL in the archive (e.g. x64\history.tlb) in BPI-MDM. This causes the CLR to load the attacker DLL at startup, enabling code execution before the legitimate application runs.



